What Is Role-Based Access Control & Why Your Portal Needs It
Learn how role-based access control can transform the way you distribute analytics to your customers through branded data portals.
Overview
Imagine managing a large organization with hundreds of employees and numerous resources. But how do you ensure that each employee has the appropriate level of access to necessary resources while maintaining security and efficiency?
How do you provide your customers with a branded analytics experience that's tailored to their unique needs?
Enter Role-Based Access Control (RBAC) through branded data portals, a powerful tool that simplifies access management, provides users with a customized analytics experience, and keeps sensitive data secure.
Understanding Role Based Access Control (RBAC)

Role-Based Access Control (RBAC) is a method of controlling user access to resources according to their respective roles within an organization, also known as role-based security.
Implementing RBAC can lead to improved security, enhanced compliance, increased efficiency, and greater transparency for organizations.
Without proper access control, organizations face risks such as data theft, system disruption, compliance violations, and difficulty in detecting policy violations.
So, what are the recommended practices for establishing role-based access control? The key lies in defining different roles and their associated permissions.
Implementing RBAC with tools can enable companies to create a secure access control environment, thereby minimizing these risks.
Additionally, in the context of a data portal, RBAC can be used to provide your data users with a tailored experience, ensuring that the data visualizations and dashboards are customized to the needs of each user.
With a well-defined role hierarchy, employees are granted access to resources based on their responsibilities and authority, ensuring that sensitive data is protected and tasks are efficiently managed.
Related Article:

The Anatomy of RBAC: Roles, Permissions, and Users
The foundation of RBAC lies in three main components:
- Roles: Roles are defined based on criteria such as job function, department, or level of authority. Associated responsibilities are determined by the permissions and actions assigned to each role.
- Permissions: Permissions denote the specific access rights or privileges that are assigned to roles or users.
- Users: Users are individuals who are assigned specific roles and permissions within the RBAC system.
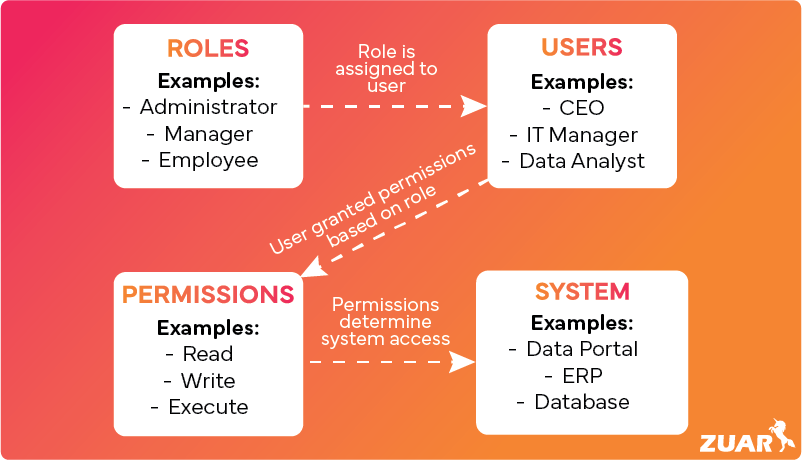
Together, these components create a secure and organized access control system that ensures users have the appropriate level of access and authority to carry out their designated tasks within an organization’s system.
For example, sales teams may have specific roles within the system, with each role granting certain permissions to access resources such as customer information, sales data, or marketing materials.
In the case of a company offering their clients a branded data portal, they can tailor their data visualizations and the branding of their portal based on the specific client that is accessing the data.
Defining Roles and Responsibilities
Roles and responsibilities in RBAC are determined according to job functions and tasks, thus optimizing the access control process.
This approach helps to prevent unauthorized access to sensitive information, reduces the risk of data breaches, and improves overall security and compliance.
To identify and assign responsibilities to roles in RBAC, it is recommended to follow a series of steps:
- Determine who needs access.
- Define responsibilities.
- Assign people to roles.
- Regularly review and update roles.
Adhering to these steps can help organizations successfully identify and assign responsibilities, ensuring that employees have the appropriate access to the resources they need to fulfill their duties.
Associating Users With Roles
In RBAC, user-role association is implemented by assigning specific roles to users within an organization. Each role is associated with a set of role permissions that dictate the actions the user is allowed to perform.
Assigning roles to users allows regulation of access to resources and functionalities according to the user’s role, providing a more streamlined and efficient management of access control within the organization.
Developing an RBAC strategy, enforcing least privilege, implementing an Identity and Access Management (IAM) system, and conducting a top-down role analysis are the recommended approaches for associating users with roles in RBAC.
These strategies help ensure that users have the appropriate level of access, as well as simplify the process of granting or revoking access as needed.

What Is a Custom Customer Portal?
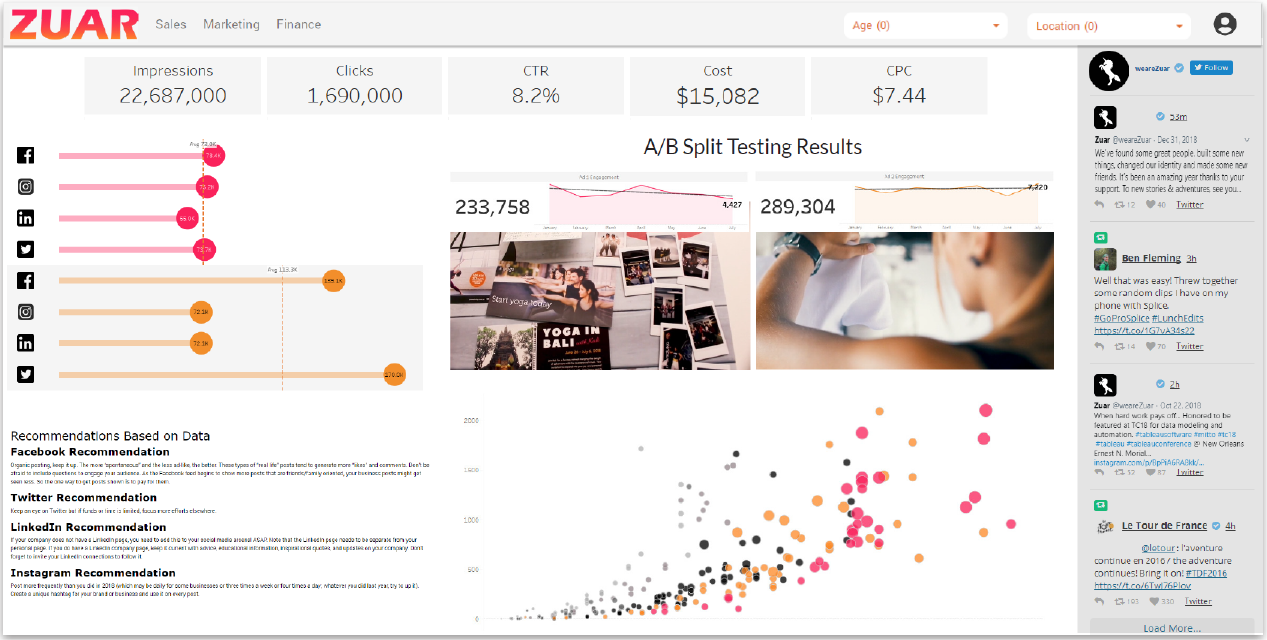
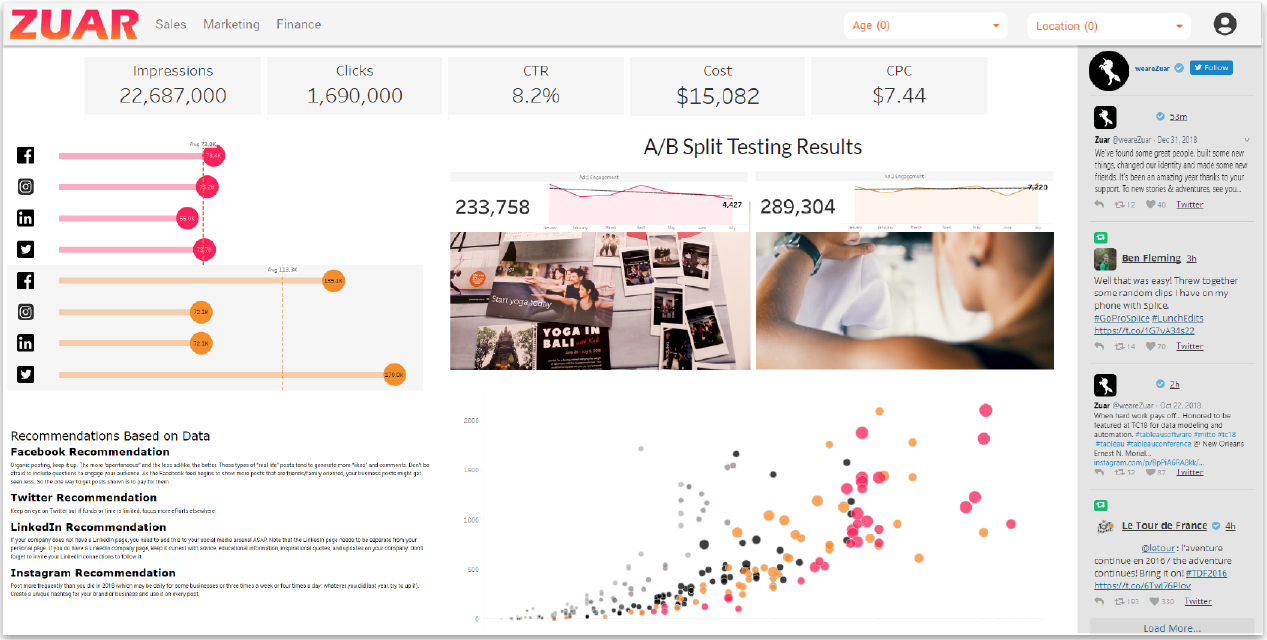
A custom customer portal (also referred to as a bespoke portal) is a centralized, white-labeled platform that allows companies to provide their clients with data analytics.
Since it's a white-label solution, the portal can be fully customized to match company branding.
It typically collects and integrates data from various sources, such as various applications, databases, and spreadsheets, offering a comprehensive view of the data.
The portal presents this complex data through easy-to-understand visuals like charts and graphs, helping users to quickly identify trends and important details.
Users can customize the portal to focus on specific information and interact with the data for more in-depth insights. Many portals also provide real-time data, which is essential for timely decision-making.
Additionally, many portals have role-based access control features, ensuring that sensitive information remains secure and is only viewed by authorized personnel based on their role.
In essence, a bespoke portal is a powerful tool that organizations can implement to give their customers unique analytics experiences.
How Bespoke Portals Simplify RBAC
Bespoke portals facilitate the implementation of role-based access control by providing a centralized platform for managing roles and permissions.
Administrators can conveniently assign roles to users and define their access levels to different data resources, thereby simplifying the process of granting and revoking access.
Furthermore, these portals often feature intuitive user interfaces and tools for managing RBAC, making it easier for administrators to configure and maintain access control policies.
Employing data portals for RBAC management offers numerous benefits, including improved data security, streamlined access management, enhanced compliance, and increased productivity.
Bespoke portals, with features such as role assignment, user management, permission management, group management, and audit logs, assist in the management of roles, permissions, and users in RBAC.
Optimizing RBAC With Zuar Portal
Zuar Portal is a branded portal solution that easily connects to Tableau, Power BI, ThoughtSpot, or other BI platforms to provide your clients with a one-stop shop for all the analytics and data visualizations they need in one place.
By implementing Zuar Portal, organizations can easily control their clients' access to their portal through roles (called 'Groups').
Within the Zuar Portal application, roles and permissions can be efficiently assigned by administrators.
Alternatively, roles can also be managed through Tableau or through an Identity Provider (IdP) being used for single sign-on (SSO) such as Okta or Active Directory.
This integration ensures seamless role synchronization and enhances the ease of managing access controls, providing a streamlined and secure user management experience.
This means that each client experiences a tailored interface, ensuring a more personalized and engaging interaction with the data.
Zuar Portal Branding & Integration
Zuar Portal's flexibility in customization extends to branding elements as well, allowing companies to integrate their own logos, color palettes, and design aesthetics seamlessly into the portal. This creates a cohesive and professional look that aligns with the company's brand identity.
Moreover, by utilizing Zuar Runner (a robust data integration platform), a variety of data sources can be integrated smoothly with existing IT infrastructure, making it a versatile and scalable solution for businesses of all sizes.
With intuitive user interfaces and comprehensive security features, the Zuar Stack empowers organizations to deliver superior data experiences to their clients, fostering trust and enhancing decision-making processes.
Learn more about Zuar Portal:

RBAC Implementation Strategies
Implementing RBAC requires careful planning, establishing a role hierarchy, and ongoing management and review of access controls.
By addressing potential challenges and maintaining clear communication throughout the implementation process, organizations can effectively manage user access to resources and ensure the security of sensitive data.
Planning Your RBAC Roadmap
A well-planned RBAC roadmap ensures a smooth implementation process and helps avoid potential issues. Developing an RBAC roadmap consists of the following steps:
- Gather perspectives from stakeholders to ensure their needs are considered.
- Define the themes and objectives of the implementation.
- Organize and prioritize tasks and milestones.
- Customize the roadmap to fit the organization’s needs.
- Adjust the roadmap based on feedback and changing requirements.
By following these steps, organizations can create a comprehensive and tailored RBAC roadmap for successful implementation.
Establishing a Role Hierarchy
A role hierarchy in RBAC is a structure that establishes relationships between roles in an organization, resembling the hierarchy of the organization.
This can simplify access control by reducing the number of unique roles to be managed, and users with senior roles in the hierarchy are granted all the permissions of their subordinates and those specific to their needs.
Establishing a role hierarchy in RBAC involves:
- Identifying the roles within the organization or system
- Determining the relationships between roles based on the organizational structure or permissions requirements
- Assigning higher-level roles to inherit permissions from lower-level roles
- Ensuring that users with senior roles have access to all the permissions of their subordinates
- Regularly reviewing and updating the role hierarchy as organizational needs change.
Managing and Reviewing Access Controls
Regularly reviewing and managing access controls helps maintain security and ensures that users have the appropriate level of access.
Access control management plays an important role in maintaining security in RBAC by assigning access and actions based on a user’s role within the system.
This ensures that employees are only given access to the information and resources that are relevant to their job responsibilities, thereby reducing the risk of unauthorized access and potential security breaches.
Implementing RBAC in a Custom Customer Portal

Implementing RBAC in a custom customer portal involves many of the same steps as implementing RBAC in any other system.
However, the beauty of solutions like Zuar Portal, is that they are designed with access control in mind, making these steps quick and easy to implement.
These steps include:
- Define User Roles: Identify different user types who will access the portal, such as administrators, analysts, managers, etc. Clearly define the access level and permissions for each role based on their needs and responsibilities.
- Map Out Permissions: For each role, specify the permissions in detail. This includes data access, features they can use, actions they can perform (like editing, viewing, or deleting data), and any restrictions.
- Integrate with User Management: The RBAC system should integrate with the portal's user management system. This includes user authentication (like login systems) and possibly linking to BI platforms or with an IdP (like Okta or Active Directory). Zuar Portal is specifically designed for these integrations.
- Implement Access Controls in the Portal: Configure the access controls in the portal. This typically involves checking the user's role and permissions before granting access to data or features within the portal.
- Test and Validate: Thoroughly test the RBAC system to ensure that it correctly restricts or allows access based on user roles. This testing should include trying to access features or data with different user accounts to validate the access controls.
- Deploy and Monitor: Once testing is complete, deploy the RBAC system. Continuously monitor the system for any unauthorized access attempts or other security issues, and make adjustments as necessary.
- Regularly Review and Update Roles and Permissions: Periodically review the roles and permissions to ensure they still align with the organization's needs and make adjustments as needed, especially when new features are added to the portal, or organizational roles change.
- Training and Documentation: Provide training for users to understand their roles and permissions. Also, maintain clear documentation for future reference and for new users.
By following these steps, you can implement an effective RBAC system in your branded analytics portal, ensuring that users have appropriate access to data and features based on their roles.

Challenges and Solutions in RBAC Deployment
While RBAC offers many benefits, there are several challenges associated with implementing and managing it effectively. These challenges can be addressed with thoughtful planning and strategic implementation:
Complex Role Definitions:
- Challenge: Defining roles can be complex, especially in large organizations with diverse job functions.
- Solution: Use a modular approach to build roles, where basic roles are defined first and then combined or extended to create more specific roles. Continuous review and adjustment of roles are necessary to keep up with changes in the organization.
Segregation of Duties (SoD) Conflicts:
- Challenge: SoD is a risk management principle that divides critical tasks and responsibilities among different people to reduce the risk of error or fraud. Ensuring that roles do not violate SoD principles can be difficult.
- Solution: Implement SoD controls during the role design phase. Use automated tools to analyze and report potential SoD conflicts.
Dynamic Access Requirements:
- Challenge: Access needs can change frequently due to factors like job changes, temporary assignments, or organizational restructuring.
- Solution: Implement processes for regular access reviews and have mechanisms in place for quick updates to roles and permissions.
Scalability Issues:
- Challenge: As the organization grows, the RBAC system must scale without becoming inefficient.
- Solution: Design the RBAC system with scalability in mind, using scalable databases and efficient algorithms for access control decisions. Zuar Portal is an example of a scalable solution that is designed for small, medium, and large businesses, meaning that the solution can grow with your business.
Compliance and Auditing:
- Challenge: Ensuring that RBAC policies comply with various regulatory requirements and facilitating audits.
- Solution: Implement comprehensive logging and reporting features. Regular audits of roles, permissions, and user assignments should be conducted.
Training and Awareness:
- Challenge: Users and administrators need to understand their roles and responsibilities within the RBAC system.
- Solution: Provide regular training and clear documentation to ensure everyone is aware of the RBAC policies and procedures.
Integration with Existing Systems:
- Challenge: RBAC systems must integrate seamlessly with existing IT infrastructure.
- Solution: Use standardized protocols and APIs for integration. Plan for interoperability during the design phase of the RBAC system. By utilizing an integration platform like Zuar Runner, integration with various other data sources is a breeze.
Addressing these challenges requires a combination of strategic planning, regular maintenance, and the use of automated tools. It's also important to adapt the RBAC system as the organization evolves to ensure it continues to meet its security and operational needs effectively.

Role-Based Access Control Next Steps
As we've illustrated, Role-based access control is an essential tool for managing user access to resources and ensuring security in various industries.
By implementing this methodology into your branded portal, you can streamline user management, enforce consistent security policies, and provide your stakeholders with easily accessible data insights.
We've also shown how you can implement RBAC quickly and easily by utilizing Zuar Portal to control user access and tailor dashboards and data visualizations to each unique role.
Turn your vision into a reality by scheduling a demo with one of our data experts.
We can quickly spin up a Zuar Portal demo that's tailored to your organization, incorporating custom branding elements and interactive dashboards that integrate data from all your data sources.
See firsthand how a custom customer portal can revolutionize your client interactions, enhancing engagement and providing a seamless, intuitive analytics experience!