Discretionary Access Control vs. Mandatory Access Control: What's the Difference?
Learn the differences between DAC and MAC, including their advantages, disadvantages, and why they're important.
Overview
There's a plethora of sensitive information in today’s digital world. Safeguarding this information against unauthorized access and breaches has become a priority in cybersecurity.
In support of this, a method known as access control can be implemented to ensure that access to sensitive data is restricted only to those with the proper authorization rights.
Access control is the first line of defense in computer security,s and it controls and manages who can access what in an organization. It is a key aspect of effective data stewardship.
Access control is split into two categories- discretionary access control and mandatory access control. The aim of both is to ensure that data remains protected, but in different ways.
In this article, we will explore both access control methods and how they differ from one another.
Key Takeaways
- Access control regulates access permissions to sensitive information to prevent unauthorized access, with mandatory access control using strict system rules and discretionary access control giving more flexibility and autonomy.
- Mandatory access control offers robust security but complex setup, making it suitable for government agencies, while discretionary access control provides flexibility for enterprise collaboration but less centralized oversight.
- In addition to mandatory and discretionary access control, role-based access control assigns permissions based on roles, and rule-based access control uses organization-defined rules to determine access.

What is Access Control?
Access control is a basic cybersecurity concept used to enforce information security. It deals with regulating, managing, and controlling access permissions of individuals to specific resources or information within a database.
The primary aim of access control is to prevent unwanted access by ensuring that only individuals with the appropriate authorizations are granted entry into the system.
In the world of cybersecurity, the concept of access control has been adopted to control and monitor access to data, applications, resources and networks in the digital space, thus enforcing security and privacy.
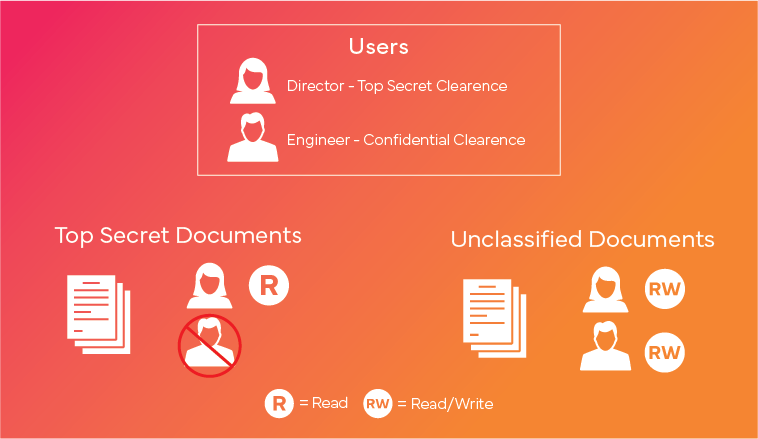
The key components that make up access control include:
Authentication
Authentication handles the verifying the identity of a user before providing access to the secured system. This component uses authentication factors like passwords, usernames and biometrics.
There are various forms of authentication, like two-factor authentication (2FA), which utilizes two authentication factors, and multi-factor authentication (MFA), which utilizes more than two authentication factors. Examples of authentication protocols include SAML and Kerberos.
Authorization
Authorization usually comes after authentication. This component helps to determine and restrict the access of a verified user to certain actions, programs, and resources after gaining entry to the system. It is often based on roles, permissions and access levels of a user’s identity.
Access Control Models
Access control adapts different models as frameworks for assigning and managing access and permissions. These models include discretionary and mandatory access control.
Access Policies
Access policies are rules set in place to dictate how access control is enforced for each individual within an organization or system.

What is Mandatory Access Control (MAC)?
Mandatory access control, or MAC, is an access control model that operates under a stringent principle, where access to resources is based on system-defined, predetermined rules and policies. This cybersecurity model places the responsibility of access control of resources on the system itself.
The fundamental goal of MAC is to ensure and enforce security by handing over authority and access control to the system rather than the users and resource owners.
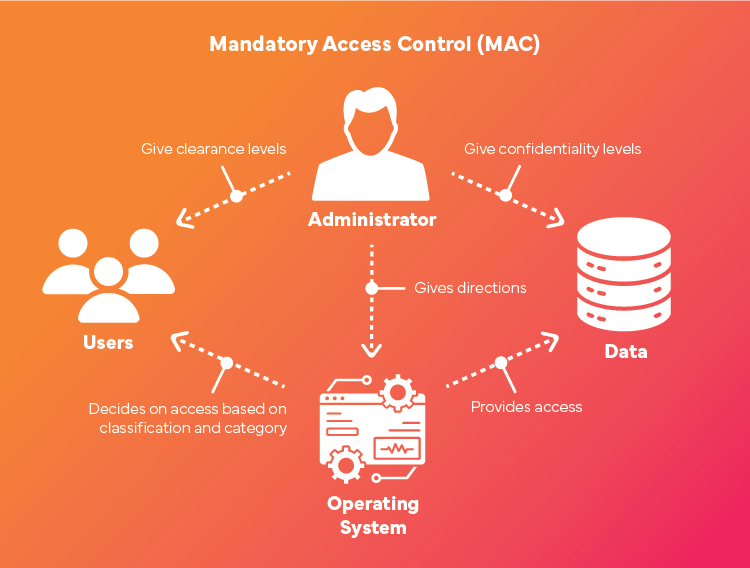
How Does Mandatory Access Control Work?
MAC uses label-based access control for data and clearance levels to manage and control access to resources. It assigns a security label to every resource in the system. These security labels/classifications are major determinants of how critical and sensitive the resource is.
These security labels such as as 'confidential, 'secret,' or 'public' are identified on resources. Clearance levels are also assigned to individuals within the organization. The clearance level that each individual is assigned will determine the resources to which they are granted secure access.
Whenever a user wants to access a resource, the system evaluates the security label and clearance level of the user to confirm if they have the appropriate clearance before access is granted.
Advantages of MAC
1. Robust Security: MAC enforces strong security measures against unauthorized access, protecting sensitive files and resources from cybercrime and unauthorized users.
2. Reduced Risk of Human Error: MAC is designed to be controlled by systems, not users or resource owners. This ensures a reduced possibility of security failure or compromise.
3. Protection Against Insider Threats: MAC helps to mitigate the risk of breaches caused by individuals who work within the organization. Adopting security labels and clearance levels controlled by the system ensures that individuals don’t misuse their privileges.
The Challenge of MAC: Complex Set-up
The setting up of MAC requires complex planning and expertise to bring the system to function as a security model on its own without significant human intervention.

What is Discretionary Access Control (DAC)?
Discretionary access control, or DAC, is a cybersecurity model that places access control authority in the resource owner's hands.
Unlike MAC, discretionary access control grants users and resource owners access to rights to their resources. This means that the resource owner gets to decide who can access certain data and who cannot.
The fundamental goal of DAC is to ensure and enforce security by handing over authority and access control to the users and resource owners rather than the systems. An example of DAC is the Unix operating system.
The main difference between discretionary access control and mandatory access control is the key factor of controlling resource access. In discretionary access control, access is controlled by the resource users, while in mandatory access control, access is controlled by the system.
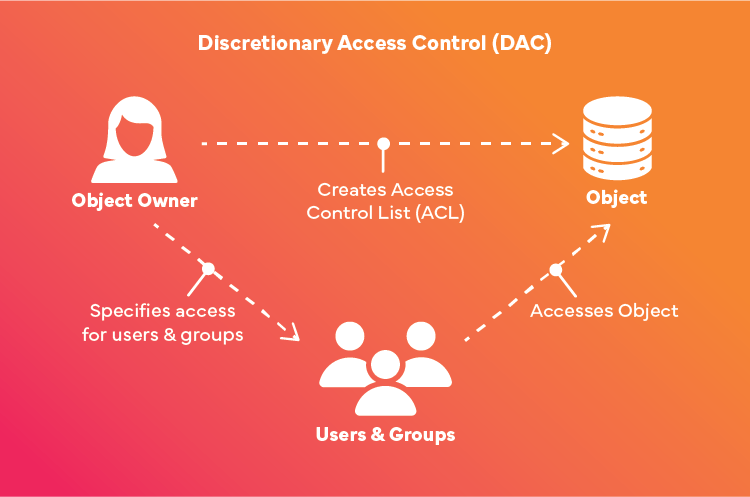
How Does Discretionary Access Control Work?
With DAC, the resource owners have the ultimate control over who gets to access the resource and who is denied it. Users can be assigned three key forms of access permissions, whether individually or in groups. These three permission types include:
- Read: This permission type allows the users to read the contents of the resources.
- Write: This permission type allows users to read and edit the file/resource.
- Execute: This permission type enables executable files to run.
Discretionary access control also allows the creation of access control lists (ACLs), which contain the list of users and the permissions assigned to each of them.
Advantages of DAC
1. Flexibility: Discretionary access control is highly flexible, in that it allows resource owners to adjust to changes and alter permissions in real time.
2. User Autonomy: DAC grants resource owners autonomy over their resources. This helps to increase efficiency and collaboration amongst the users within the organization.
The Disadvantage of DAC: User Accountability
Discretionary access control relies on the resource owners’ discretion (hence the name) to decide who gets to access their resources. It can be difficult to enforce organization-wide policies and priorities when users can share access as they see fit.
Real-World Examples of MAC vs DAC
In real-world scenarios, MAC and DAC are used in different contexts based on specific requirements for access control.
One example of MAC implementation is within government organizations, military institutions, and law enforcement agencies. These entities use MAC to secure classified information and enforce multilevel security policies and applications.
Another example involves the insurance and banking industries, where MAC is utilized to maintain better data protection, compliance, and control access to sensitive customer data.
On the other hand, DAC is commonly employed in various industries where users need more flexibility and control over access rights.
For instance, in enterprise settings, DAC allows users to configure their access parameters without the need for a system administrator, reducing administrative overheads and enabling a more responsive access control system.
These examples illustrate how MAC and DAC are used differently in real-world situations based on the need for strict control and enforcement versus user-based discretion and flexibility.

Additional Types of Access Control
Role-Based Access Control
Role-based access control is another method of access control adopted by organizations. As the name implies, it is an access control method that grants access permissions based on predefined roles of a group of individuals within the organization. These roles are based on job functions, responsibilities and organizational roles.
Role-based access control groups users with similar functions and access requirements to aid control management. Instead of assigning or revoking each individual’s access rights, any decision regarding access rights will affect the group assigned to that role.
Learn more about role-based access control:
Rule-Based Access Control
Rule-based access control is a method based on predefined rules or conditions. This access control method assigns access to resources based on the users' specific attributes, like the user's identity or the resource type. This method can be helpful when dealing with a large number of rules and conditions.

Implementing Access Control
In a rapidly evolving digital landscape, having a robust data strategy around access control is essential to ensure data security.
At Zuar, we specialize in data services that empower businesses to make informed decisions about access control strategies and technology solutions. Whether you're leaning towards the user-defined flexibility of DAC or the centralized authority of MAC, our experts are here to guide you.
Additionally, with Zuar Portal your organization can centralize it's information and analytics, making it easier to manage the access control for every stakeholder, including staff, customers, vendors, partners, etc.
Click here to try the free demo of Zuar Portal. To start a free trial and get a more in-depth experience, click here!

To learn more about Zuar's products and services, schedule a data strategy assessment with one of our data experts!